Qiuch Recon Methodology
Recon is the process by which you collect more information about your target, such as subdomains, links, open ports, hidden directories, service information, etc. In this page, I will explain my web recon methodology.
This approach may not work with all targets, as each target has its own scope. Some companies will list all their assets in scope
while others will list specific domains or subdomains. I will cover broader scopes to address all points.
Quick Note
Always use WHOIS data to verify each step. WHOIS provides information about domain name registrations, helping you confirm if an asset (like an IP or subdomain) belongs to your target.
1. Collect Acquisitions
An acquisition means the company has bought another company, and the new assets they now own, like websites or apps, are included in the bug bounty program for testing. This includes all the companies under the control of the main company.
How to Collect Acquisitions? The best website for this is Crunchbase. By searching for the company name, you can find all the acquisitions they have made. Collect this information and add it to your target scope and start recon on them.
2. Collect IPs
This involves various steps:
2.1 Collect ASNs
An Autonomous System Number (ASN) is a unique identifier assigned to a network or group of IP prefixes controlled by a specific organization or provider. By identifying the ASNs related to your target, you can uncover a range of IP addresses potentially linked to them.
However, keep in mind:
Not all IPs will be tied to ASNs directly owned by the organization, especially if they use cloud providers like AWS, Azure, or GCP.
In such cases, identifying the IPs might require deeper investigation through other means.
bgp.he.net: A great starting point. Search using the company name to find associated ASNs.
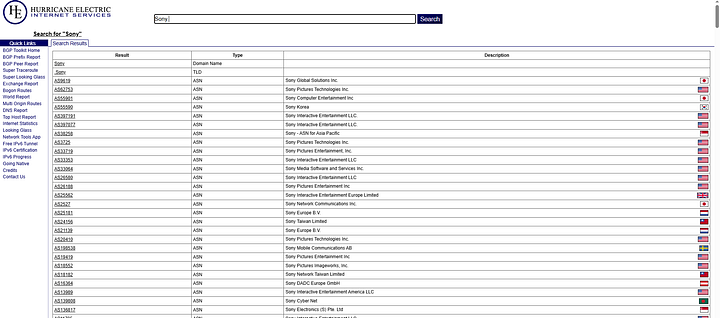
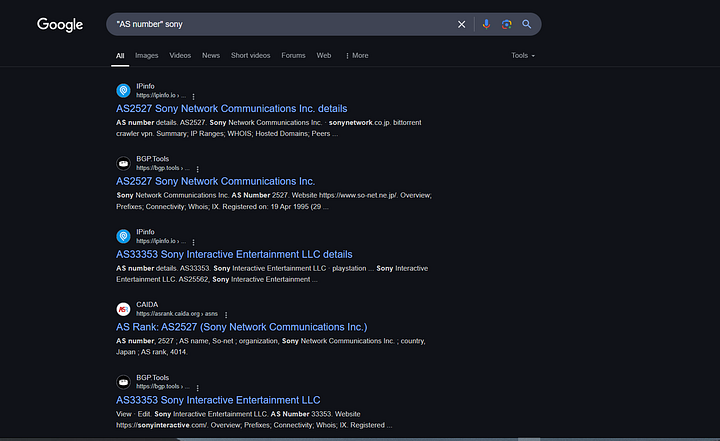
Google Dorking: Perform manual Google searches using queries like:
site:bgp.he.net <company name>"AS number" <company name>"Autonomous System" <company name>
Store the collected ASNs in a text file ( ASNs.txt ) for future use

2.2 Collect CIDRs
Once you’ve identified the ASNs associated with your target, the next step is to extract the corresponding CIDRs (Classless Inter-Domain Routing blocks) , these define specific ranges of IP addresses managed by those ASNs.
You can use the whois command with RADb (Routing Assets Database) for the ASNs stored in ASNs.txt. Run the following command:
After running this, you’ll have a list of all CIDR blocks associated with the ASN, saved in CIDRs.txt.
2.3 Find IPs from the CIDRs
To convert CIDRs to IP addresses you can run nmap with -sn option in the CDIRs.txt file :
Note: While this method is faster, it may not be the most effective. Some hosts might appear down due to firewalls blocking ping (ICMP) requests or other types of probes.
To address this, we can use masscan (which is faster than Nmap) to perform a port scan across all the CIDRs :
You can increase or decrease the --rate=250000 (the number of packets sent per second) based on your network proficiency.
Now you have all the IPs; saved in IPs.txt.
For better organization, we should put every IP running services in a single file.
Organizing IPs by Port
You can use the following Python script to organize the IPs based on the services they run:
After running the script, you will find a directory called ports_output. Inside it, you'll see the IPs organized by port, with each port's IPs saved in a separate file (e.g., 80.txt, 443.txt, etc.).
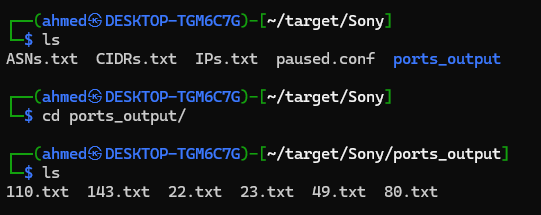
What I do after that is extract the IPs running HTTP/S services that are accessible through a browser — usually on ports 80, 443, 8080, 8443, 8000, 8888, and 5000 — and put them in a single file.
You can then run httpx on these IPs and keep the results organized.
And in my GitBook notes, under the Attack Victors by port page, i explained all the other services and their potential attacks based on the ports they run on.
3. Collect Subdmains
3.1 Subfinder
Subfinder is a subdomain discovery tool that discovers valid subdomains for websites. Designed as a passive framework to be useful for bug bounties and safe for penetration testing.
To get the most out of Subfinder, go to its config file and add your API keys from these platforms at the end of the config.yaml file:
Just sign up for accounts on these sites, and you can get your API keys from the settings section. Keep in mind that these API keys are free but have a limited number of requests, so change them out now and then.
Subfinder’s configuration file is located at:
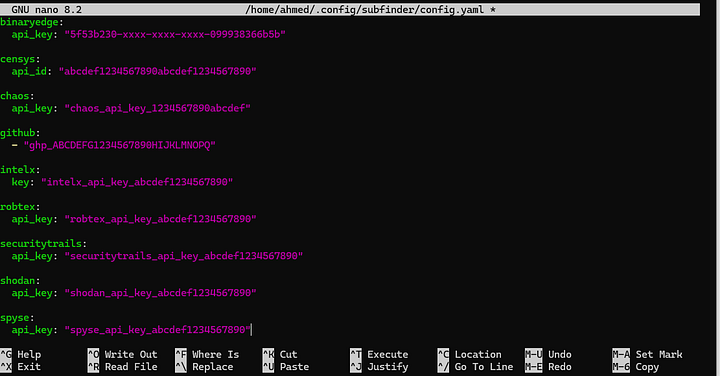
Once you’ve added the APIs, run Subfinder again and see how much more you uncover compared to before!
3.2 Amass
Amass is a powerful tool for network mapping and external asset discovery. It combines both passive and active techniques to uncover subdomains linked to a target.
For passive enumeration, you can run the following command:
This command will gather subdomains without actively probing the target.
For active enumeration, which includes brute-forcing and resolving IP addresses, use:
This command not only discovers subdomains but also gathers source information and performs IP resolution, providing a more comprehensive view of your target.
By leveraging Amass, you’ll be able to effectively uncover a wide range of subdomains, significantly enhancing your reconnaissance efforts!
3.3 Assetfinder
it can find domains and subdomains related to a given domain, and find the subdaomins of the subdaomins :
3.4 some good website
There is also some good websites like crt.sh and subdomainfinder
Last updated